We help organizations use innovative tools and tactics
to stay ahead of threat actors.
The cyber landscape evolves constantly, and so must our defenses. Generic solutions, once effective, now lag behind new threats, leaving organizations vulnerable. We bridge this gap by educating clients, implementing tailored strategies, and handling solution application, maintenance, and training.
Outcome-Focused Approach
IT Security requires constant validation and review. Our approach begins and ends with a challenging mentality. We are always evaluating our processes.
Execution and Delivery
Whether we are providing guidance, support, and oversight on the deployment of solutions in production, or overseeing services projects and training engagements, we are accountable for the delivery of the outcomes as discussed during the scoping and validation stage.
Planning and testing
Clearly defining the long-term strategy and the execution of the tactical plan is stage three of the engagement approach. Providing insight and experience we remain laser-focused on the outcome and ensuring the efficacy of the project.
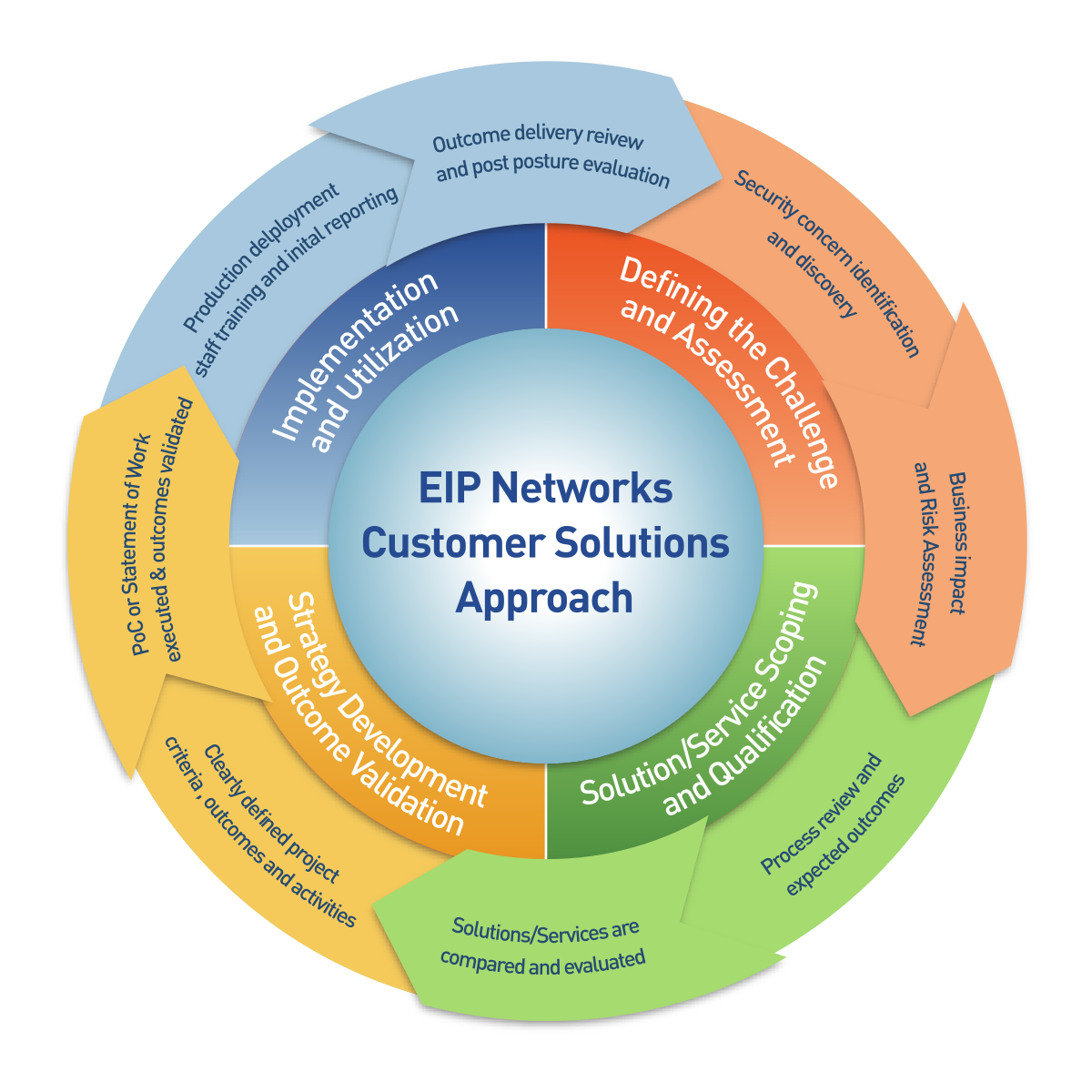
Assess and Identify
Working closely with our customers, we identify, uncover, and highlight areas of external risk and internal organizational exposure. Our goal is to improve IT security and reduce risk at all levels.
Defining the Desired Outcome
Whether it is training, services, support, guidance, or advice, we review the potential approaches required to achieve the outcome. At this point, all the potential options are explored and the best course of action is planned.
Other Tenets of Our Approach
Three R's Guarantee
Repair, replace, or refund. We stand by our work - always. If the work we perform or the solutions we sell don't deliver on the promised outcomes, we offer our three R's guarantee.
Evolving Technology
We select our technological solutions and partners based on their ability to deliver current and applicable results. By continuously testing and evaluating we are able to remain on the cutting-edge of cyber-security and help you handle real-world cyber threats.
Always Transparent
We believe that the key components of a strong partnership are transparency and accessibility. Your EIP team can be reached at any time and are ready to work. No one likes surprises. We will disclose all information regarding processes, limitations/gaps, and prices. We will not oversell, nor underdeliver.
Knowledge Sharing
We strive to share as much knowledge with our customers as possible. You can ask us anything and you will get accurate information that will help you and your organization get the best results. We want our customers to be well-informed.




